Supplier Security Assessment
In today’s digitally driven business landscape, safeguarding your organization from cyber threats extends far beyond your internal security measures. Third-party suppliers and vendors play a pivotal role in your cybersecurity posture.
If you’re wondering whether you really need to go to the expense of security assessing all your suppliers, the extra effort, and cost involved. Well, you wouldn’t be alone. But it doesn’t have to be painful. At Parnell Consulting our experts can take on that burden, provide you with an appropriate level of risk based supplier assurance, to give your customers confidence, and satisfy your industry regulators. All at fixed cost that allows you to plan your budgets and get on with running your business with confidence.
If you’re just starting to research the need for supplier security assurance, then we highly recommend you read our recent blog articles on the subject:
What We Do
Getting Started
Businesses like people are very different. The risk versus benefit decisions we make either consciously or subconsciously in our daily lives is comparable to the decisions business takes when interacting with suppliers. And equally, the risk to benefit ratio is never constant. Therefore, to conduct a supplier security assessment, you first need to understand the risk posed by that supplier. That means conducting a supplier risk assessment for each supplier.
This ensures the level of scrutiny applied to each security assessment matches the risk posed by each client-supplier relationship. And importantly, you only pay for what you need! Over the top assessments are needlessly expensive, while under assessing a supplier could very well be catastrophic.
Supplier Risk Assessment
(prior to security assessment)
Our 6 Step Approach ensures every Supplier Security Assessment is fit for purpose and cost effective.
Always following a risk-based approach that fits the client:
Step 1 Conduct suitable supplier risk assessment
Step 2 Identify and map client data, who, where, what and how.
Step 3 Identify the client’s contractual requirements.
Step 4 Identify the client’s regulatory requirements.
Step 5 Identify cyber and process threats to data posed by supplier.
Step 6 Identify the client’s exposure and what’s at stake.
The Importance of Contractual Security Requirements
The importance of good contractual security requirements cannot be overstated. If you cannot provide contractual evidence for your cyber expectations, then you have no legal grounds for complaint.
Clearly defined security requirements within supplier contracts are essential for contract management and enforcement.
Contractual Security Requirements define the expectation for information security between the client and supplier, which is often enough to provide assurance to the client that their information will be sufficiently protected. However, when dispute arises it is the contract that parties fall back on, to resolve the dispute.
It’s because supplier contractual security requirements are such an important piece of any organization’s armoury that we have devoted as separate page to the topic via the below button.
The Main Event - Supplier Security Assessment
Supplier Security Assessments on the other hand tell us two vitally important things. Firstly, can I trust this company, and secondly, can I trust their product or service, to protect my vital assets, my information?
Our standard supplier security assessment’s have been designed to fit either SaaS or Non-SaaS suppliers, with varying degrees of scrutiny depending on the risk of each supplier.
All supplier security assessments address 10 security domains as detailed below, and most importantly we only assess to the degree of risk defined by each supplier risk assessment. That means you only ever pay for what you need and equally never under assess, thereby leaving you exposed to a false sense of security.
Overview of the 10 Domains of Security Assessment
Compliance
Relating to applicable regulations and standards, have they been audited and are they in compliance.
Governance
Does a framework exist for managing information security, including policies, standards and procedures, etc
Risk Management
Does a clearly defined risk management methodology and procedures exist. How are they maintained etc.
Access Control
In depth analysis of access controls and procedures. Including JML process, RBAC, least privilege and so on.
Training & Awareness
Does a security training and awareness programme exist? Is it mandatory for all?
Data Security
What controls are in place to secure their digital assests for example networks, servers, PC’s and Mobiles.
Information Protection Processes
Relating to SDLC, Change Mgmt process, backups, documentation, email and web filtering, etc
Monitoring
Security monitoring for example malware and vulnerability scanning, log management, correlation, and so on.
Incident Response & Recovery
Do IR&R plans exist, are they regularly tested and known by all that need to know. Are they continually improved?
Data Privacy
What processes and procedures are in place to meet all applicable data privacy laws and individuals rights pertaining to PII.
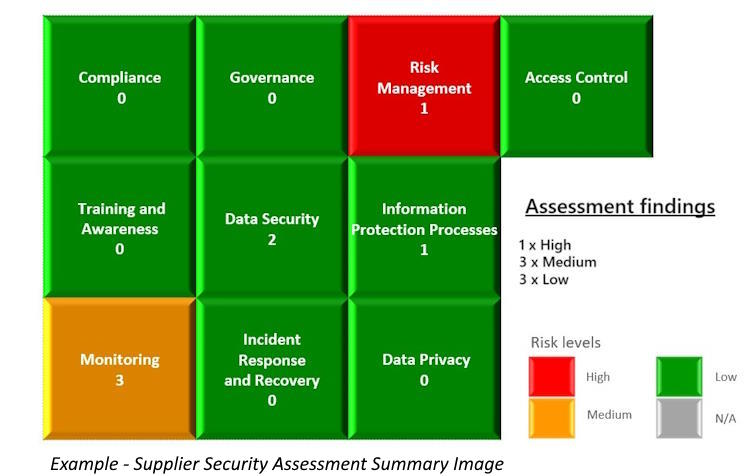
Sample Output – Medium to High Risk Supplier
For each security domain, multiple carefully designed questions have been compiled that seek to build a clear and precise picture of the suppliers security posture in each domain.
This is done through an initial introduction with the supplier to set expectations at the get go, followed by x number of iterations until a satisfactory outcome is achieved and evidence reviewed.
Following this, a report is produced in both detailed and summary format to the client.